Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help organizations like yours to prevent, detect, investigate, and respond to advanced threats.
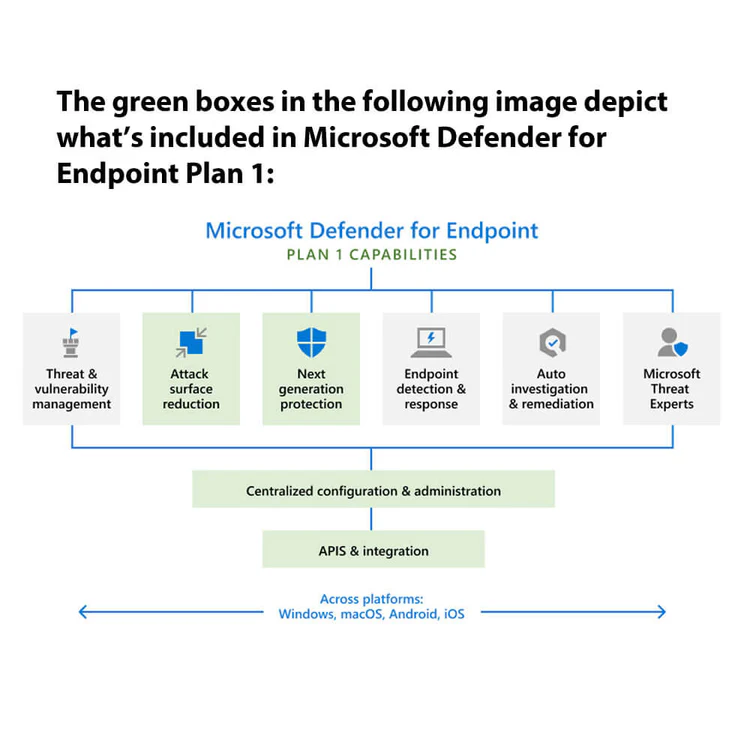
Microsoft Defender for Endpoint Plan 1 includes the following capabilities:
Next-generation protection that includes industry-leading, robust antimalware and antivirus protection
Manual response actions, such as sending a file to quarantine, that your security team can take on devices or files when threats are detected
Attack surface reduction capabilities that harden devices, prevent zero-day attacks, and offer granular control over endpoint access and behaviors
Centralized configuration and management with the Microsoft 365 Defender portal and integration with Microsoft Intune
Protection for a variety of platforms, including Windows, macOS, iOS, and Android devices
Next-generation Protection
Next-generation protection includes robust antivirus and antimalware protection. With next-generation protection, you get:
Behavior-based, heuristic, and real-time antivirus protection
Cloud-delivered protection, which includes near-instant detection and blocking of new and emerging threats
Dedicated protection and product updates, including updates related to Microsoft Defender Antivirus
Manual Response Actions
Manual response actions are actions that your security team can take when threats are detected on endpoints or in files. Defender for Endpoint includes certain manual response actions that can be taken on a device that is detected as potentially compromised or has suspicious content. You can also run response actions on files that are detected as threats. The following table summarizes the manual response actions that are available in Defender for Endpoint Plan 1.
Run antivirus scan. Starts an antivirus scan. If any threats are detected on the device, those threats are often addressed during an antivirus scan.
Isolate device. Disconnects a device from your organization’s network while retaining connectivity to Defender for Endpoint. This action enables you to monitor the device and take further action if needed.
Stop and quarantine. Stops processes from running and quarantines associated files.
Add an indicator to block or allow a file. Block indicators prevent portable executable files from being read, written, or executed on devices. Allow indicators prevent files from being blocked or remediated.
Attack Surface Reduction
Your organization’s attack surfaces are all the places where you’re vulnerable to cyberattacks. With Defender for Endpoint Plan 1, you can reduce your attack surfaces by protecting the devices and applications that your organization uses. The attack surface reduction capabilities that are included in Defender for Endpoint Plan 1 are –
Attack surface reduction rules
Ransomware mitigation
Device control
Web protection
Network protection
Network firewall
Application control
Centralized management
Defender for Endpoint Plan 1 includes the Microsoft 365 Defender portal, which enables your security team to view current information about detected threats, take appropriate actions to mitigate threats, and centrally manage your organization’s threat protection settings.
Cross-platform Support
Most organizations use various devices and operating systems. Defender for Endpoint Plan 1 supports the following operating systems:
Windows 10 and 11
Windows 7 (ESU required) Pro or Enterprise
Windows 8.1 Pro, Enterprise, and Pro Education
macOS (the three most recent releases are supported)
iOS
Android OS










Reviews
There are no reviews yet.